The Standard for Satellite Payloads
Deploy, update, and monetise satellite software like cloud operators deploy containers. 20× smaller. Hardware-isolated. Built on proven foundations.
Satellite Software Is Stuck in the 1990s
Written for Specific Hardware
Every mission is a custom integration project. Container platforms carry 200+ MB overhead — unacceptable with 512 MB RAM and 4 kbit/s uplink. RTOSes require months of porting.
Impossible to Secure
Complex codebases create large attack surfaces. The 2022 Viasat incident exploited software complexity. Memory safety vulnerabilities account for ~70% of critical bugs.
Cannot Monetise After Launch
No standard deployment model. No shared infrastructure. No app store. Operators cannot update satellites, run third-party apps, or monetise unused compute capacity.
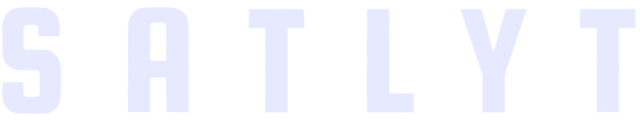
SpaceOS: Docker for Satellites
Docker succeeded because developers could type 'docker run nginx' and have a working server in seconds. SpaceOS provides the same experience for satellites: build, push, deploy with familiar tools.
But instead of Linux containers, SpaceOS runs unikernels — single-purpose VMs with hardware-backed isolation. The same application runs in 10 MB instead of 250 MB, with a fraction of the attack surface.
Validated with Thales Alenia Space: same AI application, identical outputs, 20× smaller footprint (10.2 MB vs 237.3 MB).
De-Risked from Day One
The integration is new. The building blocks are battle-tested: same network stack as Docker Desktop, same crypto as Chrome and Android, security proven by the MirageOS Bitcoin Pinata (10 BTC bounty, 150k+ attacks, zero breaches).
What SpaceOS Provides
The gap between Docker and satellites is not just portability — it's efficiency, isolation, and security. SpaceOS closes all four.
The Docker Workflow
Build OCI images, push to standard registries, deploy with a single command. Developers use familiar tools; operations teams get reproducible deployments. No custom toolchains.
20× Smaller Footprint
10 MB application images, not 250 MB container stacks. A 250 MB update takes hours over S-band; a 10 MB update takes minutes. Smaller also means cheaper, lighter hardware.
Hardware-Backed Isolation
Applications run as single-address-space VMs under KVM, Xen, or Muen — not container namespaces. Hardware enforces separation. One compromised app cannot affect others.
Formally Verified Cryptography
Post-quantum algorithms (ML-KEM, ML-DSA) via libcrux and Bertie, with mathematical proofs of correctness. The crypto is not just tested — it is proven.
Proven Use Cases
From validated pilots to production deployments

On-Board AI Processing
Validated with Thales Alenia Space
Run inference on-board, downlink insights instead of raw images. Same AI model, 20× smaller footprint, up to 37% faster inference. Saves USD 100K+ per satellite in downlink costs.
Read more
Cyber-Resilient Operations
Zero sandbox escapes in HACKSAT'25
Hardware-backed isolation, memory-safe code, post-quantum crypto. 34 participants, 8 weeks, zero breaches. Built for defence, government, and critical infrastructure.
Read more
Satellite App Store
ESA-backed, launching with OHB Hellas
Monetise unused compute capacity. Third-party apps run safely on your satellite. New revenue streams without new hardware. Ground-operational, in-orbit Q1 2026.
Read moreSee SpaceOS in Action
Two interfaces, one platform. Developers get a familiar CLI. Operators get a visual marketplace.
Build, test locally, deploy to orbit. Same workflow you know from Docker and Kubernetes.
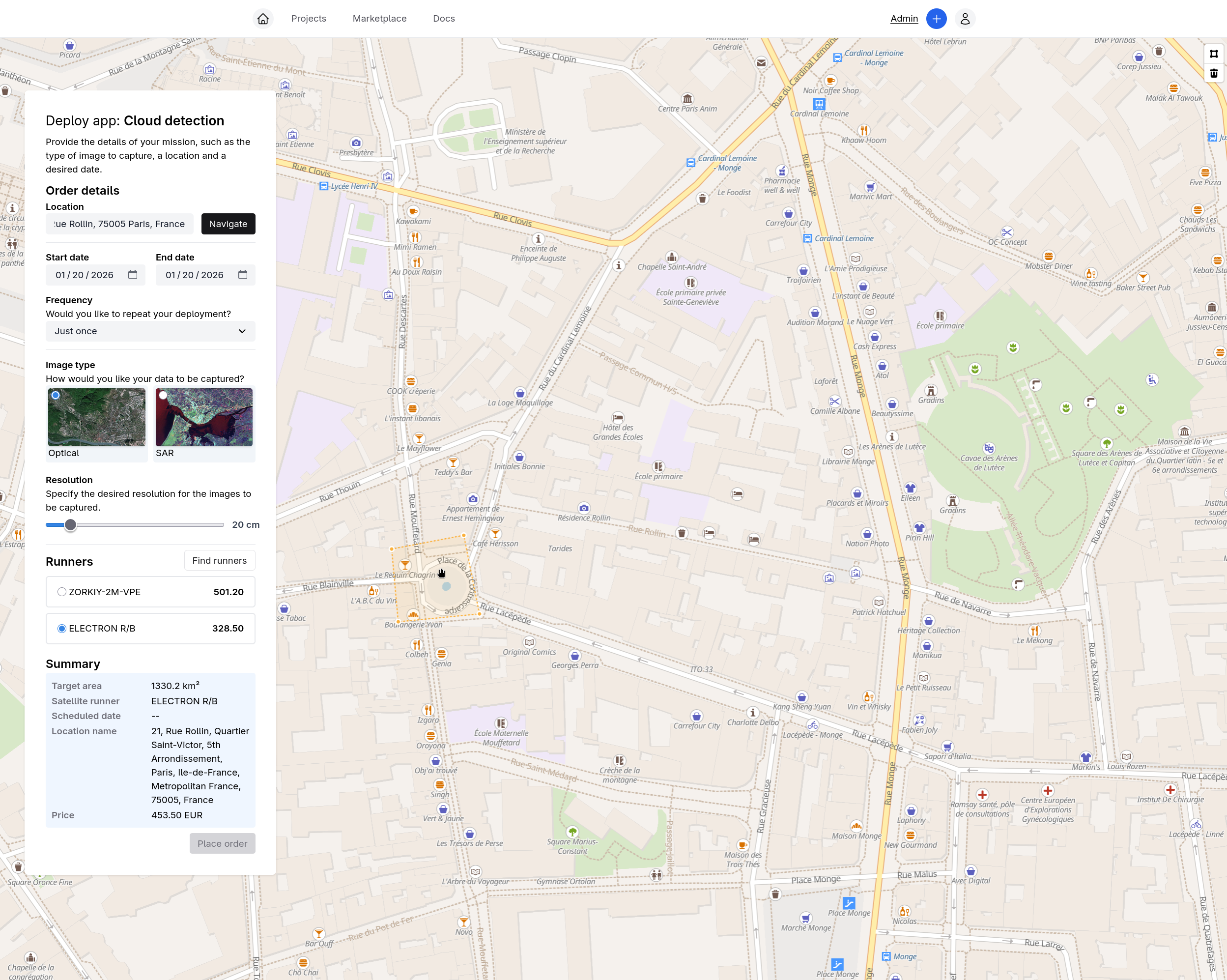
Draw your area of interest, pick an app, compare satellite runners. On-board processing cuts costs by up to 7×.
Proven & Trusted
SpaceOS is developed and deployed in collaboration with aerospace organisations across Europe, the U.S., and Australia
Funded Partnerships
EUR 1.5M+ in funded project commitments across ORCHIDE (Horizon Europe, with Thales Alenia Space), CEOS (BPI France 2030), and OSIP (ESA marketplace demonstration).
Innoflight offers SpaceOS with their CFC-400XS flight computers (200+ units). OHB Hellas provides the hardware platform for the ESA-backed Satellite App Store.
Read about Innoflight partnership →Flight Path
First payload launched March 2025 on SpaceX Transporter-13. In-orbit demonstration of the full CCSDS protocol stack on Clustergate-2, March 2026.
Three mission operators evaluating SpaceOS as their primary OS. Parsimoni was selected for Techstars Space Accelerator (Fall 2025) and incorporated in the U.S.
Read about our first launch →Technical Resources
Deep-dive documentation for technical evaluators. Contact us for early access.
SpaceOS Technical Overview
Coming SoonArchitecture, Benchmarks, CCSDS Stack, Cryptography
Deep-dive into SpaceOS internals: unikernel runtime, up to 20× smaller footprint than K3S, formally verified cryptography, and the CCSDS protocol stack with 60+ fuzz targets.
SpaceOS and Docker
OCI Compatibility Guide
How the Docker workflow maps to satellites. What transfers, what doesn't. Migration guide for container teams.
Security Architecture
Formal Verification & PQC
Post-quantum cryptography, memory safety, hardware isolation. TCB analysis and threat model for security-critical missions.
Frequently Asked Questions
Common questions from technical evaluators and investors
SpaceOS is middleware for software-defined satellite payloads. It provides a developer workflow compatible with the OCI ecosystem (build, push, deploy) and a runtime that executes applications as unikernels on hypervisor substrates — not as Linux containers. The isolation model is hardware-backed (KVM, Xen, Muen), with 20× smaller footprint than container stacks.
No. SpaceOS uses OCI for packaging — developers use familiar tools like Docker — but executes unikernels, not containers. Unikernels are single-address-space VMs that include only the code an application needs. This provides hardware-backed isolation (not namespace separation) and eliminates the Linux kernel attack surface.
SpaceOS is at TRL 4 (laboratory validation). The key components have production heritage: the network stack (mirage-tcpip) runs in Docker Desktop with millions of installations; the cryptography runs in Chrome and Android via BoringSSL; the MirageOS security model survived the Bitcoin Pinata challenge (10 BTC bounty, 150k+ attacks, zero breaches). The integration is new; the building blocks are battle-tested.
Not yet. Qualification under ECSS-Q-ST-80C is a multi-year, multi-million-euro process typically led by prime contractors for specific missions. However, OCaml (the language SpaceOS is built with) has qualification precedent: the SCADE code generator is OCaml-based and qualified at DO-178C DAL A for Airbus flight software.
Building the Future of Satellite Software
Parsimoni is raising a Series A to scale SpaceOS globally. We're looking for investors and partners who understand infrastructure software and aerospace.
Get in TouchContact Us
Interested in SpaceOS? Let's talk.